A few days ago, we told a friend about privacy issues that can be caused by instant messaging softwares like “Telegram”. His answer was usual and expected : “I have nothing secret”. But his quote inspired us to seek for other types of difficulties that such applications are prone to make. In this post, We’re going to write about a vulnerability that we’ve recently discovered in Telegram.
Undoubtedly, Telegram holds the position of the most popular instant messaging tool in Iran. According to unofficial sources: 20 million Iranians use Telegram to send/receive various types of data, including: Plain text, audio and video file.
In order to not put any obstacles in the way of the Telegram users and since at the time of writing this report the bug still exists (Has not been fixed), we’re not going to publicly pinpoint the vulnerability.
General definition of the bug:
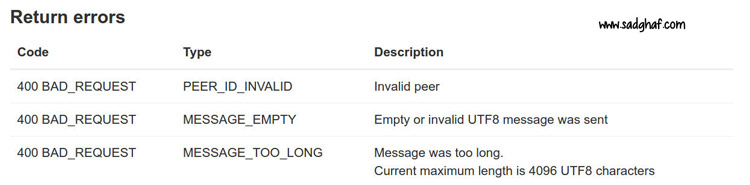
Telegram limits request rate to bar malicious users from sending a lot of messages in a short period of time. We noticed that there is also a limitation for minimum and maximum size of the text messages. The minimum limit is 1 character (1 byte) and the maximum limit is 4096. Due to a programming error in the implementation of this section, sender can get control on the size of messages and send them with arbitrary length. On the other side victim would receive all incoming messages even if they are too long.
A picture from Telegram website
Proof of concept:
In the following Telegram channel: @poc_sadghaf , You can see there are two posts that we’ve sent: the first one is 30000 bytes long (much longer than 4096 limit) and the other one is empty.
Why it is a critical security issue?
Assuming that each ASCII character is one byte long, attacker can send multi-million-character long strings to victims (or just a null message to be funny!) and the victim would receive the message without taking a scratch!? It’s like downloading a large file without accepting to receive it (Like being an actual server)!
During the test process we noticed two alarming outcomes:
1-A lot of bandwidth was being taken.
Considering that by default Telegram uses mobile data (If other networks are not being used) it can be really harmful for the receiver.
2-The device crashes or just stop working due to lack of space (or memory).
Summing up what we’ve said, It’s possible to get up unusually late (perhaps because your phone has crashed and the alarm didn’t work :D) and see that your phone faced with insomnia last night, because it has downloaded tens of gigabytes of data (text messages). And the worse part is yet to come: Due to the Telegram policy, It’s not necessary to have a user in your contact list in order to receive a message from him. So an attacker can use an anonymous phone line to carry out the attack.
We hope we have had a small role in the process of informing people (especially in our country) about damaging consequences of using such applications. Which is like to play role of a server while having resources of an ordinary client.